Zimbra Open Core Series – Rate Limiting Email with PolicyD
Rate Limiting Email Using PolicyD
PolicyD is a built-in, open-source tool in Zimbra that allows you to implement spam combating and email compliance features. In this post, I will show you how to set up outgoing email rate limiting, which can help you keep your email server and domains in good standing with public blacklists.
This example is one of many things you can do (and probably not the only thing you should do) to avoid being blacklisted.
Real-world example: SMB wants to implement a mailing policy
Recently a Zimbra SMB customer asked if it was possible to prevent users in their company from sending out mass emails from the company’s Zimbra mailserver. They want to implement a policy to use an external service like Mailchimp to send out these emails from a different email domain to keep their Zimbra server in good standing (a business-critical concern).
PolicyD can help. It can be set up with policies to define the maximum number of email recipients a user can send to in a specific period.
This example introduces and educates you in the ways of PolicyD. It is in no way meant to be a drop-in production-ready solution. Please use it responsibly and run it in a test environment.
The script below has been tested on a CentOS 7 single server Zimbra 8.8.15 installation.
- Download the install script on your test environment.
wget https://raw.githubusercontent.com/Zimbra-Community/zimbra-tools/master/cbpolicyd.sh -O /tmp/cbpolicyd.sh
chmod +rx /tmp/cbpolicyd.sh
Read the contents of cbpolicyd.sh for an understanding of how the setup works. Please note that you probably want to modify it to install on a MariaDB server outside of your Zimbra server, as that way, your data is preserved on Zimbra upgrades.
2. When you are ready, run the installer:
./tmp/cbpolicyd.sh
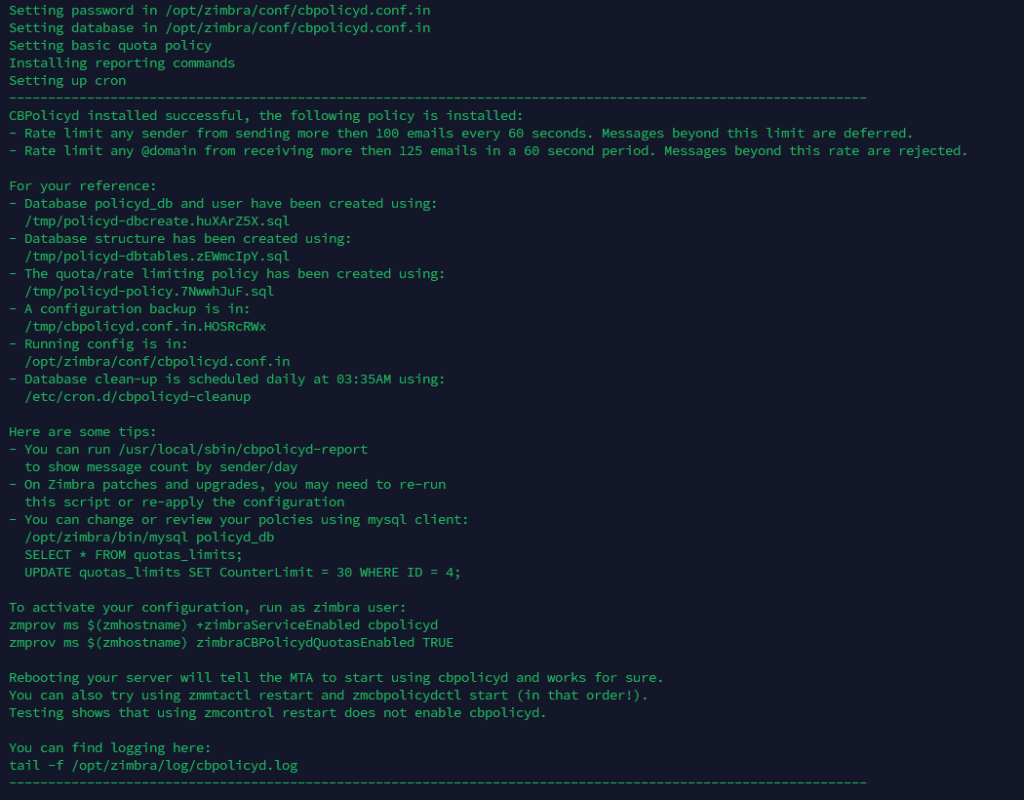
After running the default setup, the following policy is installed:
* Rate limit any sender from sending more than 100 emails every 60 seconds. Messages beyond this limit are deferred.
* Rate limits anyone from receiving more than 125 emails in 60 seconds. Messages beyond this rate are rejected.
3. Enable and start the cbpolicyd service on Zimbra:
su zimbra zmprov ms $(zmhostname) +zimbraServiceEnabled cbpolicyd zmprov ms $(zmhostname) zimbraCBPolicydQuotasEnabled TRUE zmmtactl restart && zmcbpolicydctl start
4. To test the configuration, temporarily change the outgoing email rate to a lower number, so you can observe if the email is rejected.
/opt/zimbra/bin/mysql policyd_db SELECT * FROM quotas_limits; UPDATE quotas_limits SET CounterLimit = 1 WHERE QuotasID = 3;
The above may be a bit confusing if you have no experience in relational databases. To find the correct `QuotasID`, do a `SELECT * from quotas;` and look at the `ID` from the `Sender:user@domain` record. Now try to send 2 emails to yourself in one minute to ensure the second is rejected.
Bonus Tip
When accounts are compromised, the above policies will not help. Instead of looking at emails per minute, it is better to configure policies that count per hour by setting the corresponding Period to 3600 in the quotas table. You can also customize the error message in the Zimbra UI (hidden under the details button) by setting the corresponding data field in the quotas table.