ConfigServer Security & Firewall (csf)
Installing ConfigServer Firewall
Step 1: Downloading
Config Server Firewall is not currently available in Debian or Ubuntu repositories, and has to be downloaded from the ConfigServer’s website.
wget http://download.configserver.com/csf.tgz
This will download CSF to your current working directory.
Step 2: Uncompressing
The downloaded file is a compressed from of tar package, and has to be uncompressed and extracted before it can be used.
tar -xzf csf.tgz
Step 3: Installing
If you are using another firewall configuration scripts, such as UFW, you should disable it before proceeding. Iptables rules are automatically removed.
UFW can be disabled by running the following command:
ufw disable
Now it is time to execute the CSF’s installer script.
cd csf
sh install.sh
The firewall is now installed, but you should check if the required iptables modules are available.
perl /usr/local/csf/bin/csftest.pl
The firewall will work if no fatal errors are reported.
Note: Your IP address was added to the whitelist if possible. In addition, the SSH port has been opened automatically, even if it uses custom port. The firewall was also configured to have testing mode enabled, which means that the iptables rules will be automatically removed five minutes after starting CSF. This should be disabled once you know that your configuration works, and you will not be locked out.
Basic Configuration
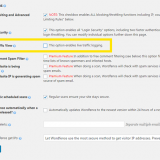
CSF can be configured by editing its configuration file csf.conf in /etc/csf:
nano /etc/csf/csf.conf
The changes can be applied with command:
csf -r
Step 1: Configuring ports
The less access there is to your VPS, the more secure your server is. However, not all ports can be closed as the clients must be able to use your services.
The ports opened by default are the following:
TCP_IN = "20,21,22,25,53,80,110,143,443,465,587,993,995" TCP_OUT = "20,21,22,25,53,80,110,113,443" UDP_IN = "20,21,53" UDP_OUT = "20,21,53,113,123"
Services using the open ports:
- Port 20: FTP data transfer
- Port 21: FTP control
- Port 22: Secure shell (SSH)
- Port 25: Simple mail transfer protocol (SMTP)
- Port 53: Domain name system (DNS)
- Port 80: Hypertext transfer protocol (HTTP)
- Port 110: Post office protocol v3 (POP3)
- Port 113: Authentication service/identification protocol
- Port 123: Network time protocol (NTP)
- Port 143: Internet message access protocol (IMAP)
- Port 443: Hypertext transfer protocol over SSL/TLS (HTTPS)
- Port 465: URL Rendesvous Directory for SSM (Cisco)
- Port 587: E-mail message submission (SMTP)
- Port 993: Internet message access protocol over SSL (IMAPS)
- Port 995: Post office protocol 3 over TLS/SSL (POP3S)
It is possible that you are not using all of these services, so you can close the ports that are not used. I would recommend closing all ports (removing port number form the list), and then adding the ports you need.
Below are port sets that should be opened if you are running the listed service:
On any server:
TCP_IN: 22,53 TCP_OUT: 22,53,80,113,443 UPD_IN: 53 UPD_OUT: 53,113,123
Apache:
TCP_IN: 80,443
FTP server:
TCP_IN: 20,21 TCP_OUT: 20,21 UPD_IN: 20,21 UPD_OUT:20,21
Mail server:
TCP_IN: 25,110,143,587,993,995 TCP_OUT: 25,110
MySQL server (if remote access is required)
TCP_IN: 3306 TCP_OUT: 3306
Note: If you are using IPv6 for your services, you should also configure TCP6_IN, TCP6_OUT, UPD6_IN, and UPD6_OUT similarly to how IPv4 ports were configured earlier.
You can find a comprehensive list of TCP and UDP ports on Wikipedia. You should open the ports of all the services you use.