OPTIONS
-h, --help
Show this message
-l, --status
List/Show the IPv4 iptables configuration
-l6, --status6
List/Show the IPv6 ip6tables configuration
-s, --start
Start the firewall rules
-f, --stop
Flush/Stop firewall rules (Note: lfd may restart csf)
-r, --restart
Restart firewall rules (csf)
-q, --startq
Quick restart (csf restarted by lfd)
-sf, --startf
Force CLI restart regardless of LFDSTART setting
-ra, --restartall
Restart firewall rules (csf) and then restart lfd daemon. Both
csf and then lfd should be restarted after making any changes to
the configuration files
--lfd [stop|start|restart|status]
Actions to take with the lfd daemon
-a, --add ip [comment]
Allow an IP and add to /etc/csf/csf.allow
-ar, --addrm ip
Remove an IP from /etc/csf/csf.allow and delete rule
-d, --deny ip [comment]
Deny an IP and add to /etc/csf/csf.deny
-dr, --denyrm ip
Unblock an IP and remove from /etc/csf/csf.deny
-df, --denyf
Remove and unblock all entries in /etc/csf/csf.deny
-g, --grep ip
Search the iptables and ip6tables rules for a match (e.g. IP,
CIDR, Port Number)
-i, --iplookup ip
Lookup IP address geographical information using CC_LOOKUPS set-
ting in /etc/csf/csf.conf
-t, --temp
Displays the current list of temporary allow and deny IP entries
with their TTL and comment
-tr, --temprm ip
Remove an IP from the temporary IP ban or allow list
-td, --tempdeny ip ttl [-p port] [-d direction] [comment]
Add an IP to the temp IP ban list. ttl is how long to blocks for
(default:seconds, can use one suffix of h/m/d). Optional port.
Optional direction of block can be one of: in, out or inout
(default:in)
-ta, --tempallow ip ttl [-p port] [-d direction] [comment]
Add an IP to the temp IP allow list (default:inout)
-tf, --tempf
Flush all IPs from the temporary IP entries
-cp, --cping
PING all members in an lfd Cluster
-cg, --cgrep ip
Requests the --grep output for IP from each member in an lfd
Cluster
-cd, --cdeny ip [comment]
Deny an IP in a Cluster and add to each remote /etc/csf/csf.deny
-ctd, --ctempdeny ip ttl [-p port] [-d direction] [comment]
Add an IP in a Cluster to the temp IP ban list (default:in)
-cr, --crm ip
Unblock an IP in a Cluster and remove from each remote
/etc/csf/csf.deny and temporary list
-ca, --callow ip [comment]
Allow an IP in a Cluster and add to each remote
/etc/csf/csf.allow
-cta, --ctempallow ip ttl [-p port] [-d direction] [comment]
Add an IP in a Cluster to the temp IP allow list (default:in)
-car, --carm ip
Remove allowed IP in a Cluster and remove from each remote
/etc/csf/csf.allow and temporary list
-ci, --cignore ip [comment]
Ignore an IP in a Cluster and add to each remote
/etc/csf/csf.ignore. Note: This will result in lfd being
restarted
-cc, --cconfig [name] [value]
Change configuration option [name] to [value] in a Cluster
-cf, --cfile [file]
Send [file] in a Cluster to /etc/csf/
-crs, --crestart
Cluster restart csf and lfd
--trace [add|remove] ip
Log SYN packets for an IP across iptables chains. Note, this can
create a LOT of logging information in /var/log/messages so
should only be used for a short period of time. This option
requires the iptables TRACE module and access to the raw PRE-
ROUTING chain to function
-m, --mail [email]
Display Server Check in HTML or email to [email] if present
--rbl [email]
Process and display RBL Check in HTML or email to [email] if
present
-lr, --logrun
Initiate Log Scanner report via lfd
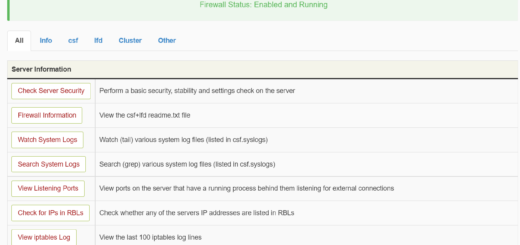
-p, --ports
View ports on the server that have a running process behind them
listening for external connections
--graphs [graph type] [directory]
Generate System Statistics html pages and images for a given
graph type into a given directory. See ST_SYSTEM for require-
ments
--profile [command] [profile|backup] [profile|backup]
Configuration profile functions for /etc/csf/csf.conf
You can create your own profiles using the examples provided in
/usr/local/csf/profiles/
The profile reset_to_defaults.conf is a special case and will
always be the latest default csf.conf
list
Lists available profiles and backups
apply [profile]
Modify csf.conf with Configuration Profile
backup "name"
Create Configuration Backup with optional "name" stored in
/var/lib/csf/backup/
restore [backup]
Restore a Configuration Backup
keep [num]
Remove old Configuration Backups and keep the latest [num]
diff [profile|backup] [profile|backup]
Report differences between Configuration Profiles or Configura-
tion Backups, only specify one [profile|backup] to compare to
the current Configuration
--mregen
MESSENGERV2 /etc/apache2/conf.d/csf_messenger.conf regeneration.
This will also gracefully restart httpd
--cloudflare [command]
Commands for interacting with the CloudFlare firewall. See
/etc/csf/readme.txt and CF_ENABLE for more detailed information
Note: target can be one of: An IP address; 2 letter Country
Code; IP range CIDR. Only Enterprise customers can block a Coun-
try Code, but all can allow and challenge. IP range CIDR is lim-
ited to /16 and /24
list [all|block|challenge|whitelist] [user1,user2,domain1...]
List specified type of CloudFlare Firewall rules for comma sepa-
rated list of users/domains
add [block|challenge|whitelist] target [user1,user2,domain1...]
Add CloudFlare Firewall rule action for target for comma sepa-
rated list of users/domains only
del target [user1,user2,domain1...]
Delete CloudFlare Firewall rule for target for comma separated
list of users/domains only
tempadd [allow|deny] ip [user1,user2,domain1...]
Add a temporary block for CF_TEMP seconds to both csf and the
CloudFlare Firewall rule for ip for comma separated list of
users/domains as well as any user set to "any"
-c, --check
Check for updates to csf but do not upgrade
-u, --update
Check for updates to csf and upgrade if available
-uf Force an update of csf whether and upgrade is required or not
-x, --disable
Disable csf and lfd completely
-e, --enable
Enable csf and lfd if previously disabled
-v, --version
Show csf version